Hardware & Firmware Overview
Communication scheme
Hardware
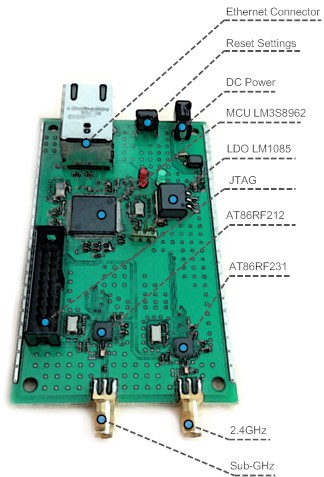
The hearth of the Open Sniffer is LM3S8962 (ARM Cortex-M3) microcontroller. This micro is quite exceptional because it implements 100Mbit Ethernet controller with fully PHY and MAC layer on the chip. Radio interface consists of two 802.15.4 radio transceivers AT86RF212 / AT86RF212B (sub-gigahertz band) and AT86RF231 (2.4 GHz band). These chips were selected based on the best receiver sensitivity, the lowest energy consumption and comprehensive feature set. Interconnection between radios and microcontroller is handled via fast SPI interface. The uniqueness of the sniffer lies in a timestamp marking. This can be done precisely (microseconds range) thanks to dedicated I/O pin in radio modules and input capture unit in the MCU. Schematics might be downloaded here.
Firmware
Firmware architecture is depicted in the picture below. Radio modules AT86RF212/231 are controlled by the RF driver. When the RF driver receives a new 802.15.4 frame it is immediately marked by the timestamp. Then the frame is encapsulated to the ZEP (ZigBee Encapsulation Protocol) and buffered. Although the ZEP protocol is natively included in the Wireshark it is recommended to use newer version ZEPv3. Finally, the buffered ZEP packet is sent via UDP to its destination. Open Sniffer is configured via web interface implemented in Mini HTTP server. For this task the LwIP (Lightweight TCP/IP) stack is involved. The current firmware supports TCP/IP v4.
Firmware Architecture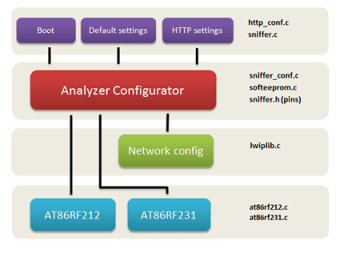
Firmware Layers

